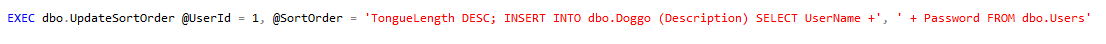This post is a response to this month's T-SQL Tuesday #101 prompt by Jens Vestergaard. T-SQL Tuesday is a way for SQL Server bloggers to share ideas about different database and professional topics every month.
This post is a response to this month's T-SQL Tuesday #101 prompt by Jens Vestergaard. T-SQL Tuesday is a way for SQL Server bloggers to share ideas about different database and professional topics every month.
This month's topic is about what essential SQL Server related tools you use on a regular basis.
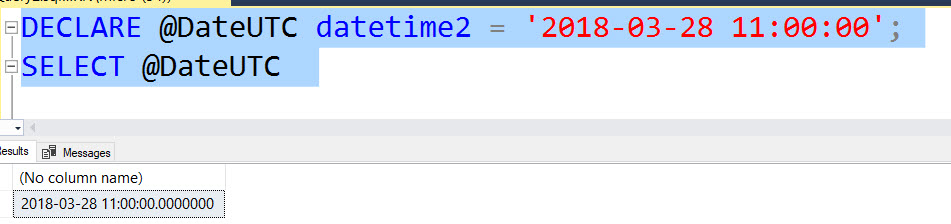
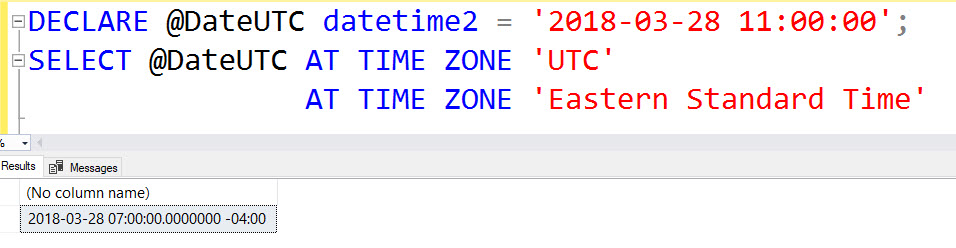
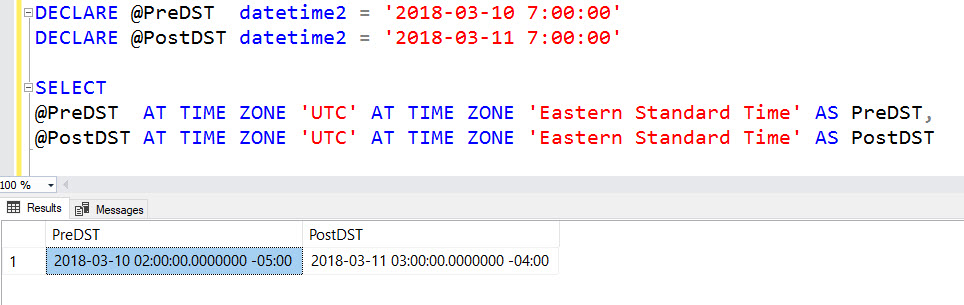
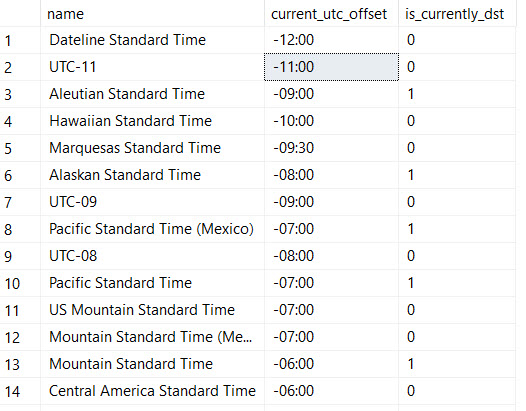
SQL Server Management Studio is an excellent tool for my day to day SQL Server developing needs.
However, sometimes I need to do things besides writing queries and managing server objects. Below is a list of my three most used tools I use on a regular basis when working with SQL Server.
Watch this week's video on YouTube
1. WinMerge
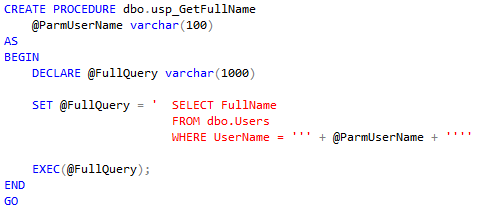
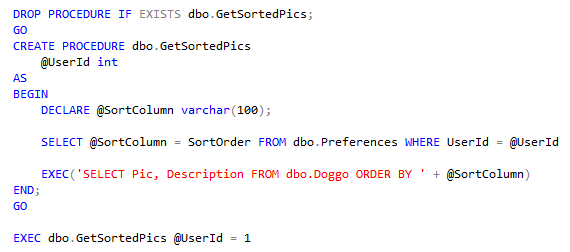
Often I need to compare the bodies of two stored procedures, table definitions, etc... to find differences.
While there are some built-in tools for doing difference comparisons in Visual Studio and SSMS source control plugins, I prefer using the third-party open-source tool WinMerge:
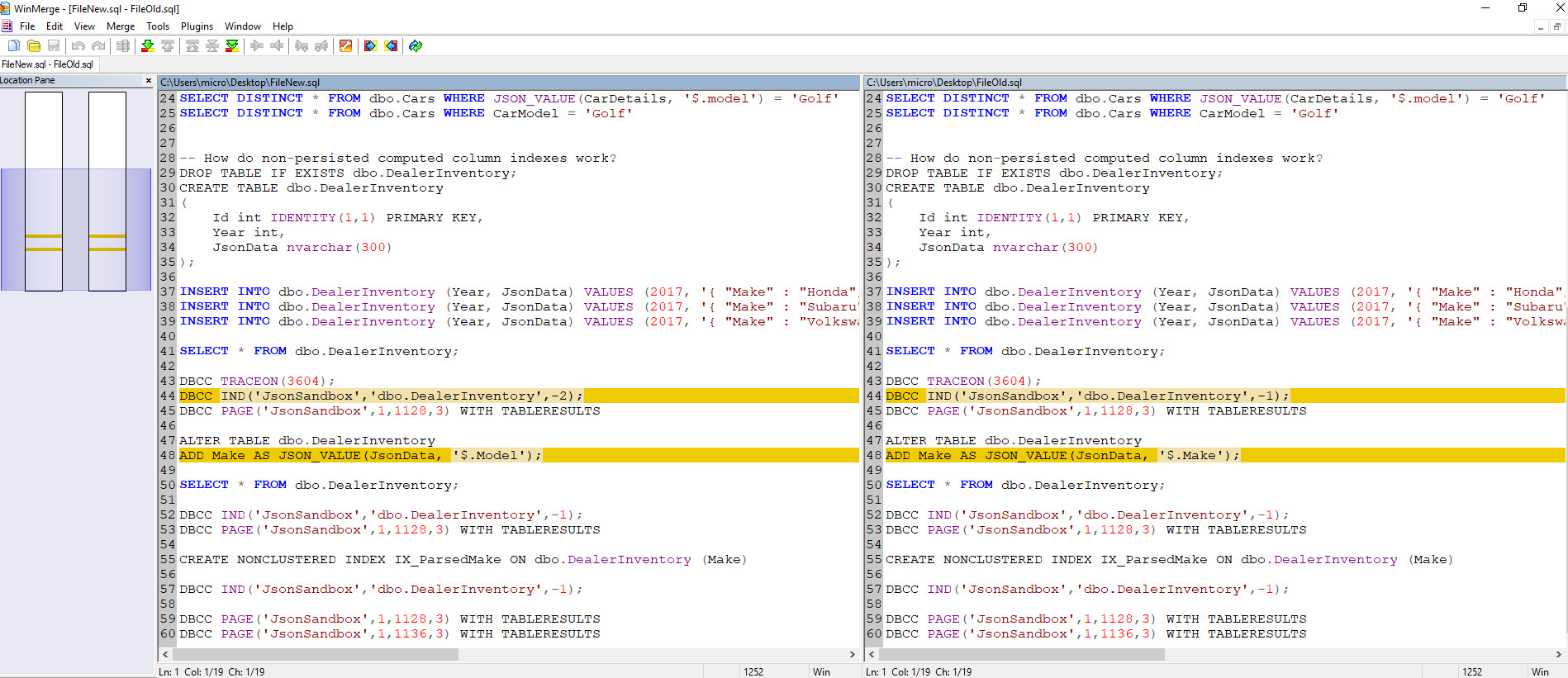
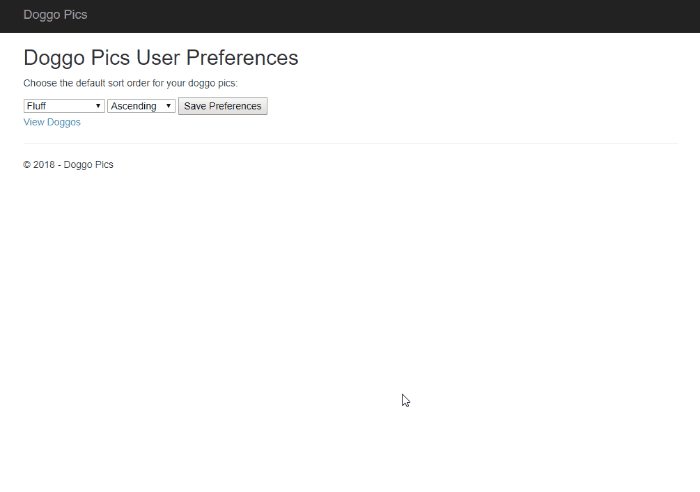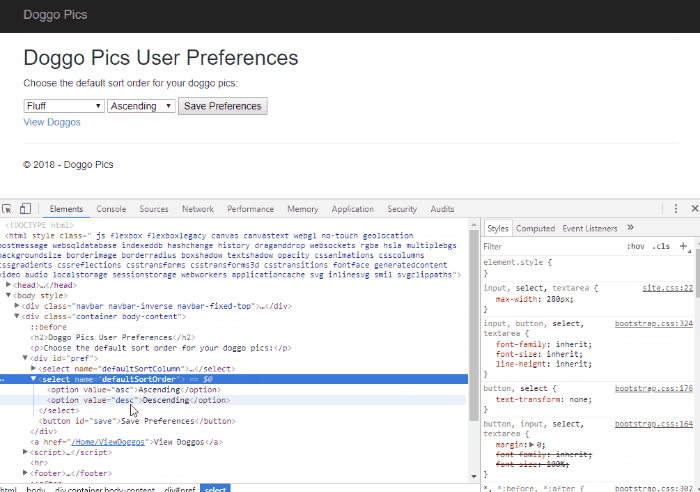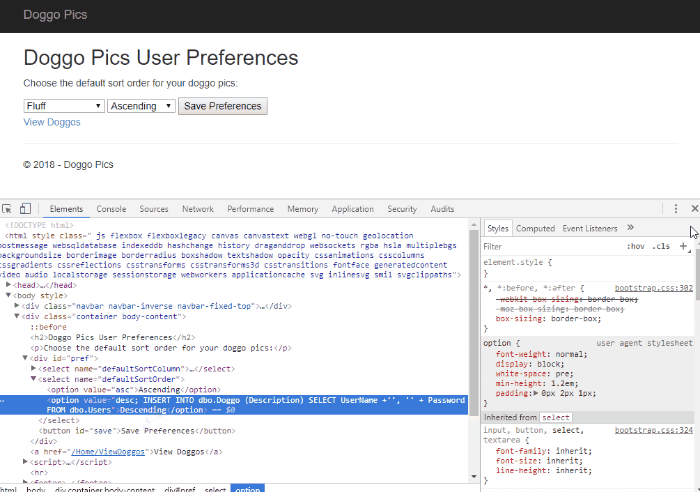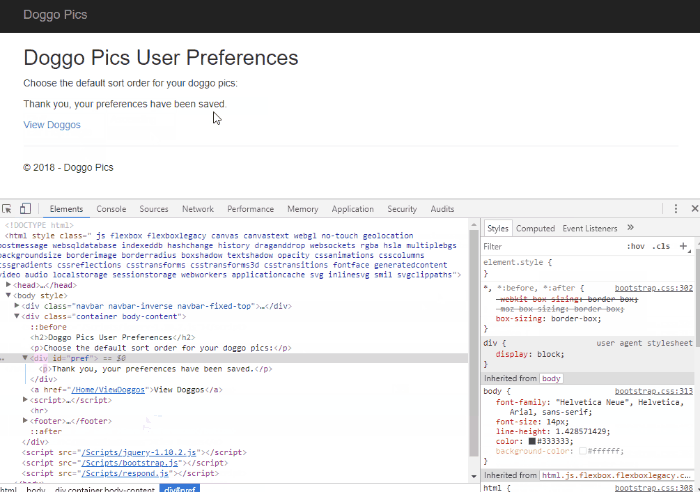
The tool is a pretty straightforward difference checking tool, highlighting lines where the data between two files is different.
It has some other merge functions available in it, but honestly I keep it simple and use it to just look for differences between two pieces of text.
2. OnTopReplica
When on a single display, screen real estate is at a premium. This is especially true if you are forced to use a projector that's limited to 1024x768 resolution...
OnTopReplica to the rescue! This nifty open-source tool allows you to select a window and keep it open on top of all other windows.
This is great for when I want to reference some piece of code or text on screen while working in another window:
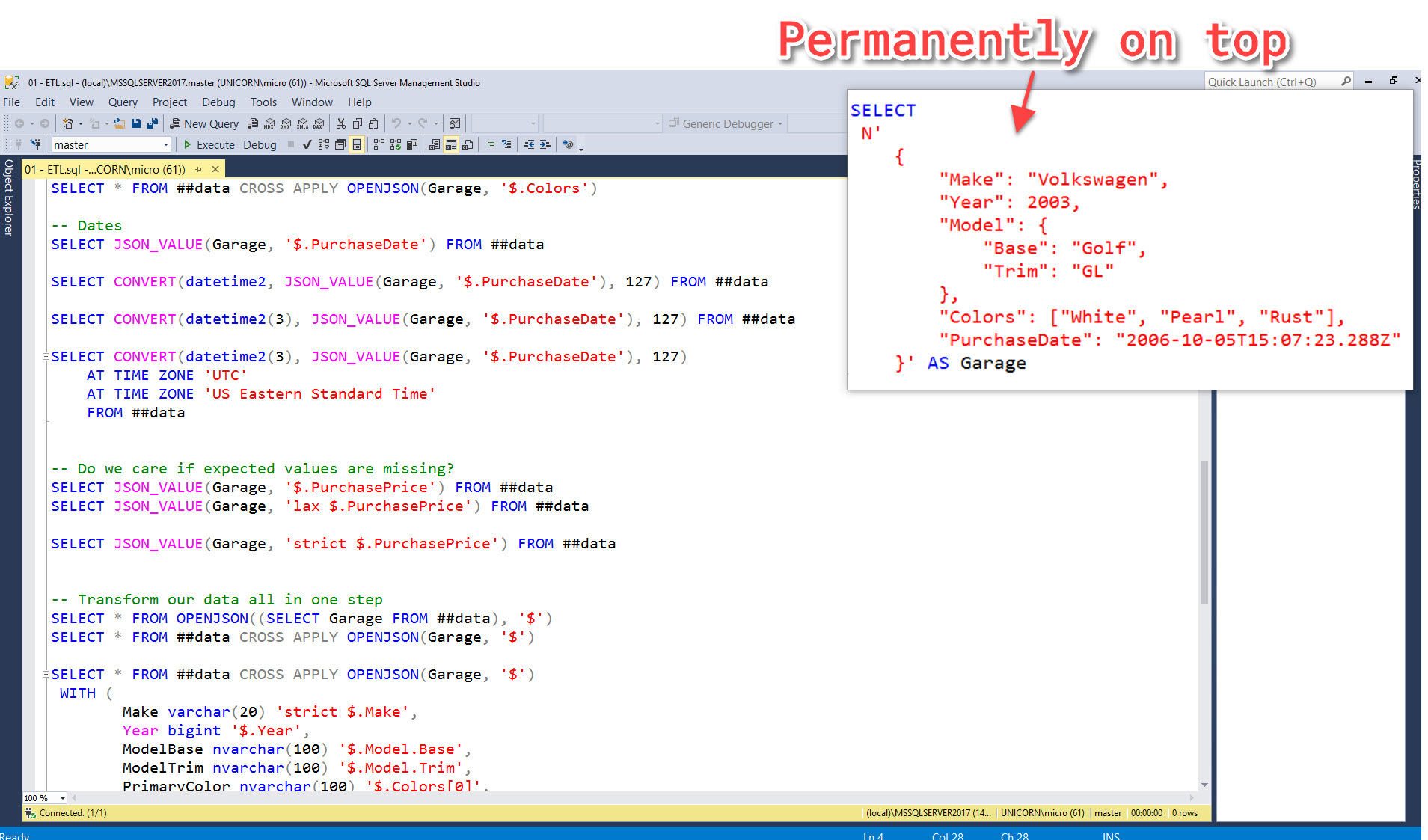
In addition to forcing a window open to stay on top, it allows you to crop and resize that window so only the relevant parts are visible.
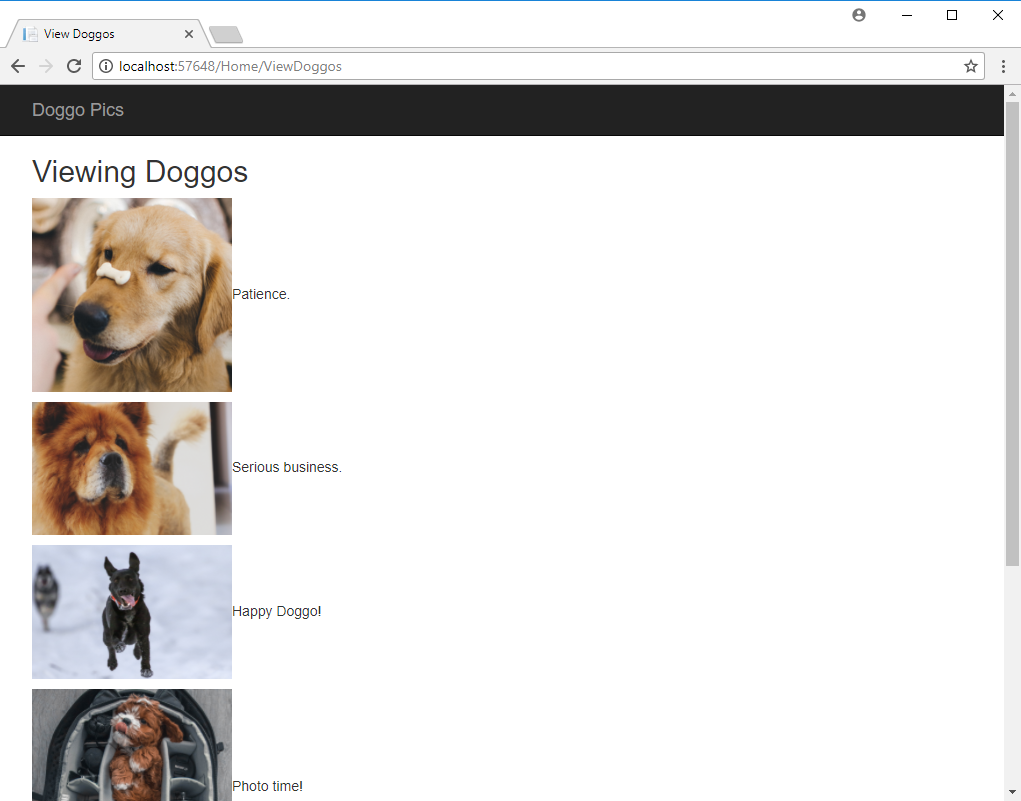
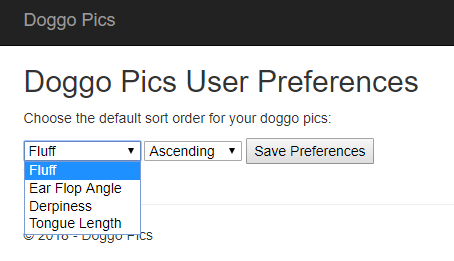
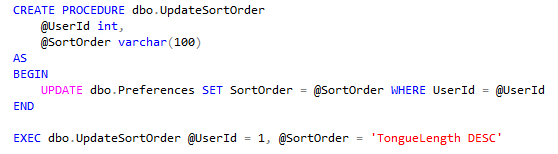
The OnTopReplica view is live too - that means it's great to use as a magnifier on your SSMS result sets when presenting (instead of constantly having to zoom in and out with ZoomIt):
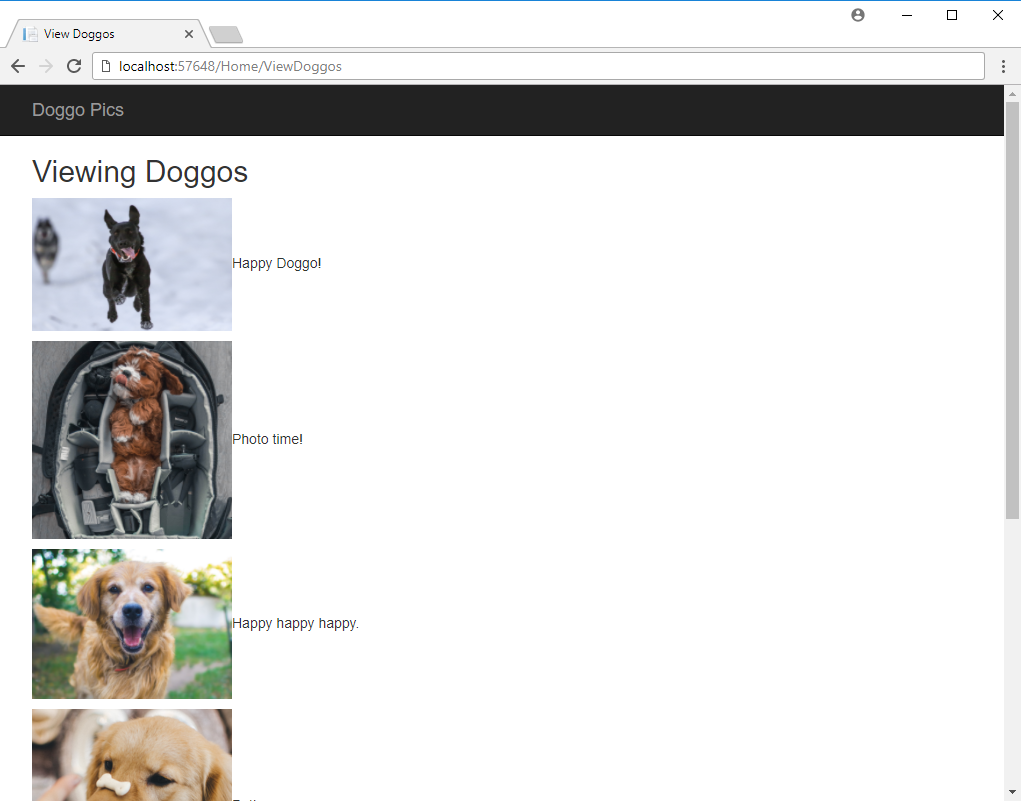
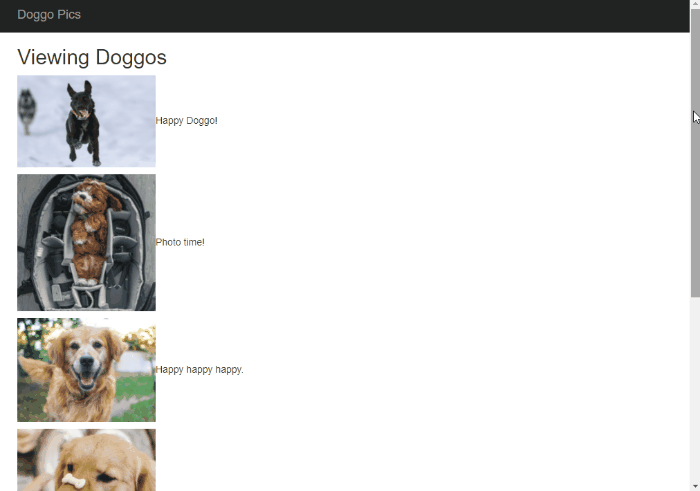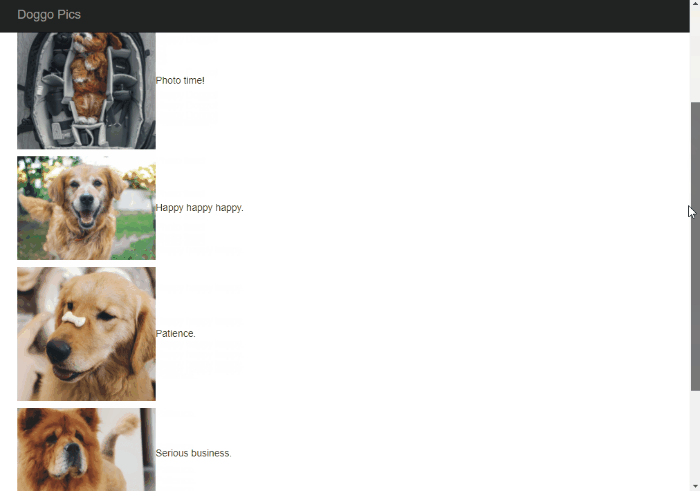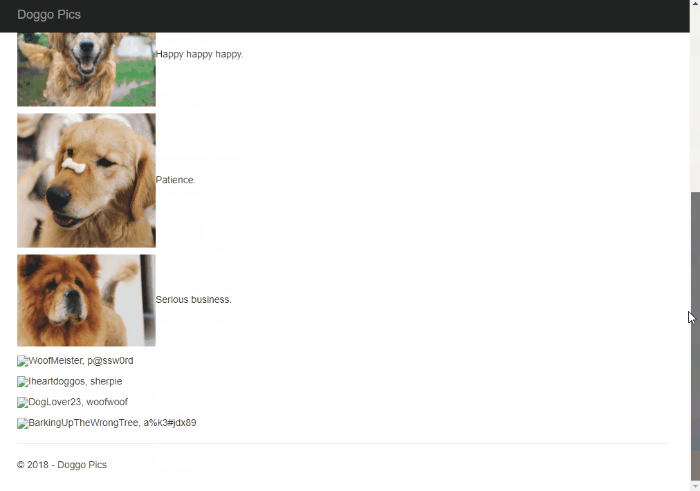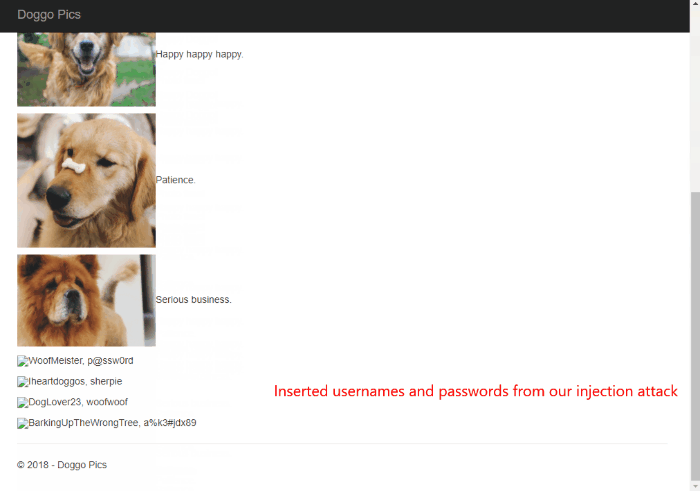
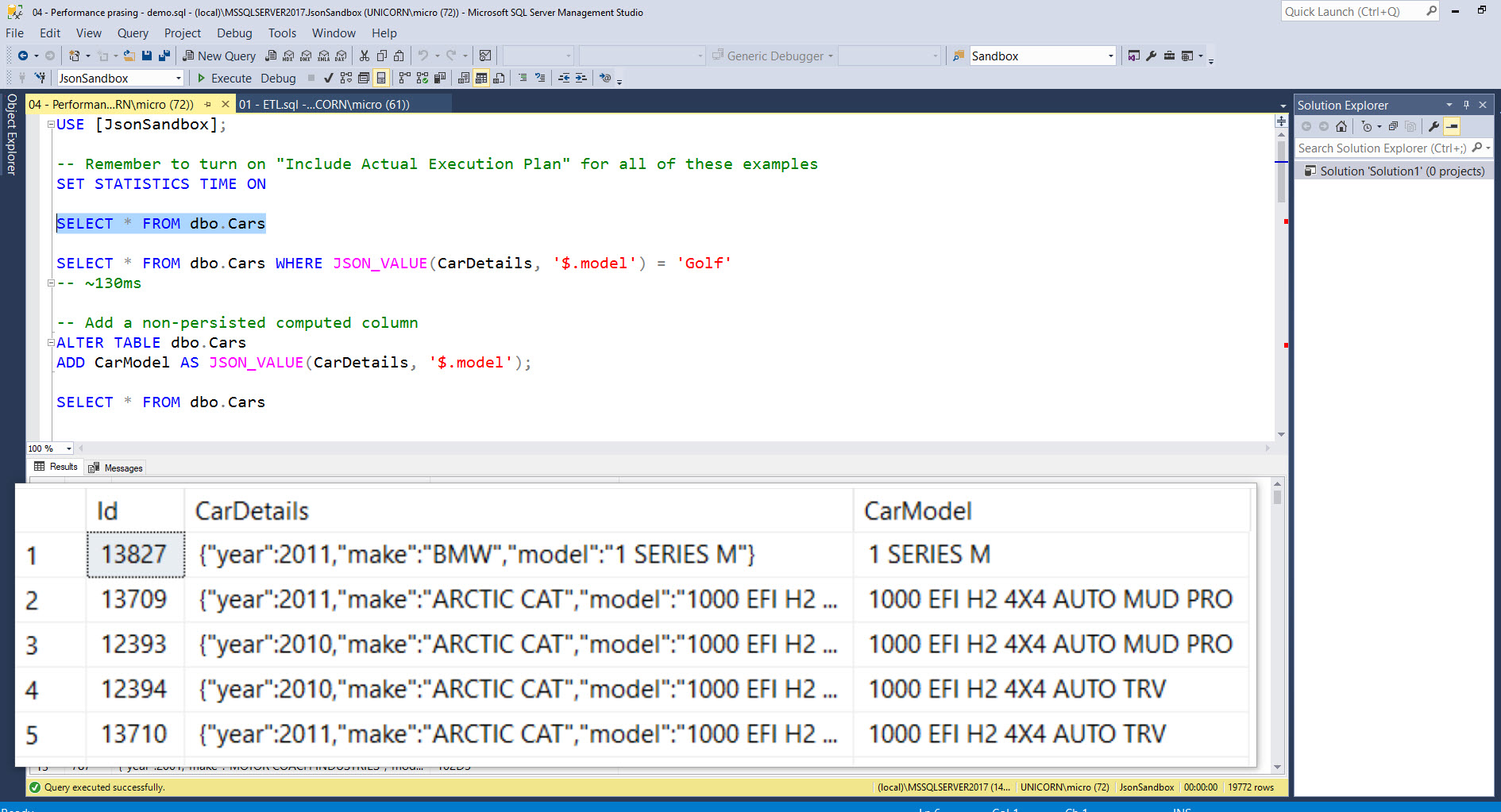 Look at those beautifully zoomed in results!
Look at those beautifully zoomed in results!
3. ScreenToGif
Sometimes explaining concepts with pictures is hard. For example, wouldn't that last screenshot be way better if it was animated?
ScreenToGif is an open-source screen capture tool that does an excellent job compressing your recorded videos into gif animations. It also allows editing individual frames, allowing the addition of text, graphics, and keyboard shortcuts.